California based Gurkirat Singh discovered a way to gain access to anyone’s Facebook profile using a security flaw in the social networking giant’s password reset mechanism. The social networking giant uses an algorithm that generates a random 6-digit passcode ? that’s 10? = 1,000,000 possible combinations. According to him, Facebook needs to store duplicate codes for multiple users if more than 1,000,000 users request a password reset. This means that more than two people have the same passcode. To use this for his purpose, Gurkirat Singh devised a way to send in 2 million password change requests to Facebook.
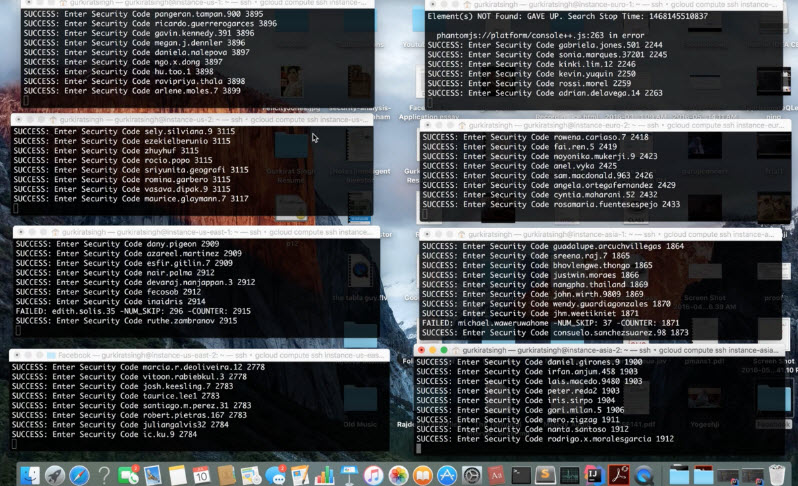
— Gurkirat Singh (@GurkiratSpeca) August 25, 2016 Since Facebook IDs are 15-digit long, Singh used 1,00,000,000,000,000 and made queries to Facebook Graph API to see which IDs were valid. This can only be done through authorized apps, and once a match is found, you can enter the ID in the URL like www.facebook.com/[ID]. The URL then automatically changes the ID to the username. This data was compiled into a JSON by Singh. To handle the problem of IP changing, Gurkirat Singh simply used a proxy server that listened to HTTP Requests and then assigned a random IP address to each request. He used a multithreaded script to simulate user behaviour when a passcode is required. The script requests a passcode to every user in the JSON file created earlier. Then the scripts were run to make the requests. It looked like this:
After doing so, the 6-digit passcode needs to be matched using the Brute force technique. Singh added ID to the key ‘u’ and the successfully matched passcode to the key ‘n’ in the URL as www.beta.facebook.com/recover/password?u=…&n=… Doing so returned a match. Once this was done, Singh added this matched passcode to the URL and was redirected to the password reset page. Singh immediately informed Facebook but to his surprise, Facebook security engineers designated this as a low priority risk and awarded in a token $500 bug bounty.